PENETRATION TESTING
what is penetration testing?
A penetration test, also called a pen test, simply means evaluating IT vulnerabilities that could be exploited by hackers in an organization’s applications, operating systems, and devices. This assessment is essential for the cybersecurity strategy as you identify but you also validate security defenses.
WHY IS PENETRATION TESTING IMPORTANT?
Risk Assessment
A Pen test can help you identify which channels in your business are the most at risk and how they can influence your business. This is how penetration testing solution providers can help you assess the main system weaknesses and take actions accordingly.
Regulations and Compliance
For many companies, a penetration system is mandatory if they perform activities that need to comply with certain laws. For example, if you want to be PCI compliant, you will need to do application penetration testing to ensure the regulations are followed correctly.
Competition
Getting hacked can have extremely serious consequences and it can affect the success of your company. Having all your data on the screens of your competitors is as easy as a click of a button.



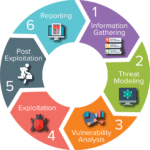
What Are The 5 Stages Of The Penetration Test?
01: Planning & Preparation
In the first stage, before we start the penetration test we need to determine the goals we want to achieve at the end of the testing, what systems will be tested, what the test types will be, who will be responsible for each, and other important details that need to be determined.

02: DISCOVERY
In this step, the penetration testers will try to discover as much information for your company as possible in order to understand the potential vulnerabilities of these. Such information is IP addresses, network domains but also more personal data such as names and job titles.

03: Penetration Attempt
After we gather the information we need, we then decide what attacks will be made. In this step, it is important to answer a three questions.
– What are the biggest vulnerabilities?
– What threats are the most critical?
– What are the most suitable steps that I need to follow to defend against the threats?
04: Reporting
After the pen tests have run successfully, we create a detailed report in which we contain all the findings and insights we discovered in the preview steps. In this report, we include the weaknesses on the systems, the threats, and the recommendations of how to fight those threats.

05: Remediation
In this phase, we clean any footprint that is left from the testing, and the remedy to fix the weaknesses of the infrastructure begins. If weaknesses cannot be remediated then other controls are needed to be established to ensure the protection of these weaknesses.
How can we Help you?
We at MarkiTech.AI, an AI app development company, are qualified to complete automated penetration testing to protect your business from cyber threats. With our highly technical engineers and developers, we help you examine the strengths and weaknesses of your systems and by following a proven methodology, we tailor our services to match and satisfy your goals.
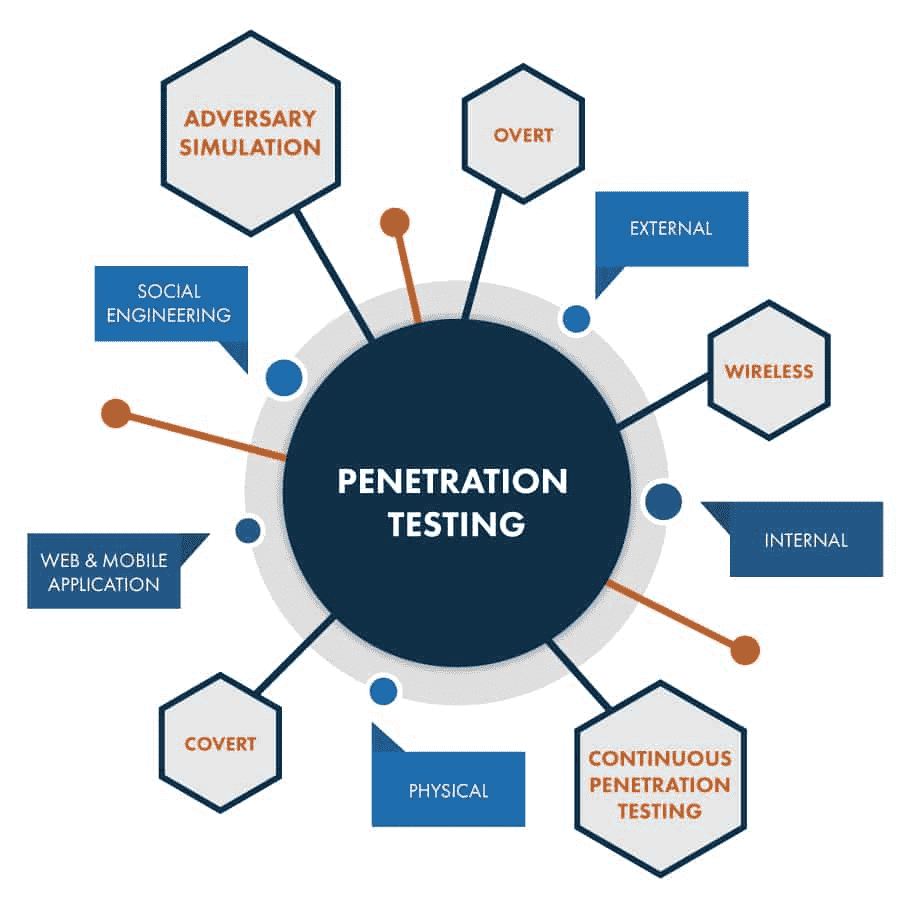
Types of Penetration Testing that we Provide at MarkiTech.AI
Previews Penetration
Testing MarkiTech.AI
Completed
Recomendations
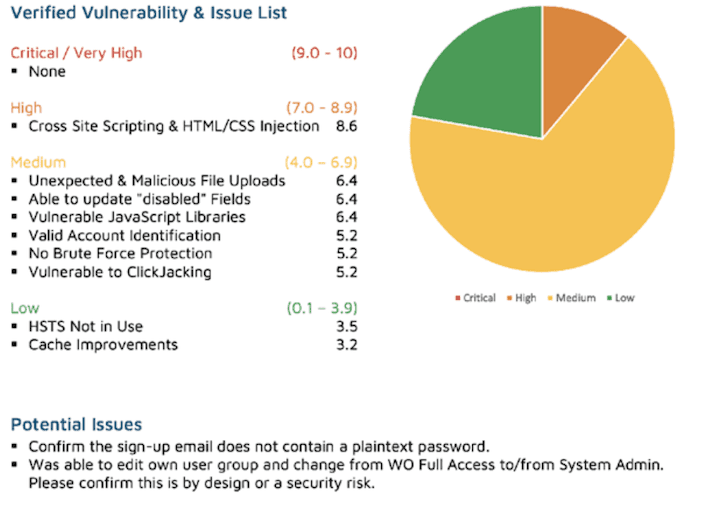
The following recommendations provide direction on improving the overall security posture of X web application:
- Ensure that the login to X includes a limited number of login attempts before enforcing a lockout protocol. As currently implemented, the login page permits brute force attacks and password guessing. The same holds for the other login / registered user accounts. A suggested maximum of 5 failed login attempts for the implementation of a timeout on the order of 15 minutes: suggested maximum of 10 failed login access attempts for an account lockout.
2. Cross-site scripting and HTML/CSS code injection issues were identified. These can lead to session hijacking and potentially other high-risk attacks. Remediation of this can be accomplished by implementing content security policies and encoding HTML content appropriately before storing it into a database.
3. The potential for uploading of malicious or unexpected files was discovered. This could include viruses and possibly executable code to other networks / users: i.e.: the transfer of malware. This can be resolved by creating a white-list of acceptable file types and blocking all other types. Ensure that this cannot be bypassed by using .ZIP or encrypted files.
4. Disabled fields could be updated. This would allow fields not intended for use to be activated and used for malicious intent. This issued can be remedied by implementing a backend validation process for all disabled fields.
5. The application was determined to use vulnerable JAVASCRIPT libraries. These need to be updated to prevent a compromise of the application.
6. The entire site (all pages) is vulnerable to a process called clickjacking. This allows a malicious actor to create a “look-alike” page that users would then click on or else enter keystrokes, allowing HTML content prior to the malicious person to capture the content and use it in subsequent attacks against the target. This can be resolved by applying appropriate security headers
Testing Approach
All testing was executed in several related phases.
- In the planning phase, the rules of engagement were identified, scope of testing and test windows were agreed upon, and testing goals were set.
- The discovery phase included automated vulnerability scanning along with manual testing to explore and understand the testing target and any vulnerabilities that could be detected by automated tools.
- The attack phase comprised efforts to exploit any vulnerabilities detected, and to synthesize knowledge gained about the environment, its technology, its users and its function into an escalation of privilege beyond that intended by the customer.
- The final phase recorded all findings in a manner that supports risk assessment and remediation by the customer. This included the writing of this report.
Discovery and reconnaissance
As the first step of this engagement, MarkiTech performed discovery and reconnaissance of the environment. This included performing network or application scans; reviewing the system, network architecture; or walking through a typical use case scenario for the environment. The results of discovery and reconnaissance determine vulnerable areas which might be exploited.
Validation and exploitation
MarkiTech used the results of the reconnaissance efforts as a starting point for manual attempts to compromise the Confidentiality, Integrity and Availability (CIA) of the environment and the data contained therein.
The highest risk vulnerabilities identified were selectively chosen by the assessor for exploitation attempts. More detailed results of these exploitation and validation tests were provided.
Penetration Attempt
After we gather the information we need, we then decide what attacks will be made. In this step, it is important to answer a three questions.
– What are the biggest vulnerabilities?
– What threats are the most critical?
– What are the most suitable steps that I need to follow to defend against the threats?