Remote Patient Monitoring (RPM) is employed by healthcare providers to collect patient statistics data remotely using internet-based technologies. This digital health technology is usually employed for patients with chronic or pre-existing medical conditions, needing regular monitoring, and for whom in-person visits might be cumbersome and non-essential.
Remote wellness monitoring involves third-party platform providers utilizing videoconferencing capabilities and leveraging cloud and internet technologies coupled with RPM devices to capture a patient’s biometric data. The resulting information is then relayed to physicians, who use it to evaluate and treat their patients. It further allows a two-way communication between the patient and healthcare provider to enhance the continuum of care. Given its remote features, RPM has presented a unique opportunity to improve accessibility, especially during the pandemic.
While there is increased adoption of these virtual capabilities, the issue of data security in healthcare has long been contended. It is aggravated by the lack of familiarity and poor implementation of security protocols. Thus, it is critical to ensure that the infrastructure employed by RPM and conserves the integrity and confidentiality of patient’s data, while ensuring the safety of patients.
Below, we discuss some of the relevant security risks facing RPM.
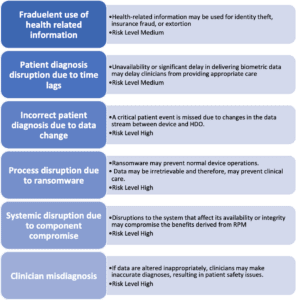
RPM Risks
Risk is defined as a measure of the extent to which an entity is threatened by potential circumstance or event, and is typically a function of:
(i) the adverse impacts that would arise if the circumstance or event occurs
(ii) the likelihood of occurrence
In the context of RPM, a 2020 National Institute of Standards and Technology (NIST) publication divides risks into cybersecurity risks and privacy risks.
Cyber Security Risks
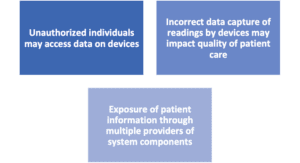
Privacy Risks
RPM Security Framework
Given that Remote Patient Monitoring and other digital health solutions’ security risks are broadly divided into cybersecurity and privacy risks, the National Institute of Standards and Technology details two separate security frameworks.
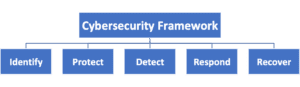
Cybersecurity Framework:
i) Identify
Under the Identification framework, organizations undertake asset management and risk assessment.
Asset Management:
This includes inventory management of physical devices, systems, software platforms and applications within the organization. Further there is cataloging of external information systems as well as prioritizing resources such as hardware, devices, data, time, personnel, and software, based on their classification, criticality, and business value.
Risk Assessment:
To assess risk, organizations need to identify and document asset vulnerabilities, and potential business impacts and likelihoods. They need to determine risk through use of threats, vulnerabilities, likelihoods, and impacts, along with identification and prioritizing of risk responses.
ii) Protect
Under the protection framework, organizations identity management, authentication and access control, enhance data security, drive information protection, conduct maintenance and employ protective technology.
Identification of Management, Authentication and Access Control:
This will allow organizations to issue, manage, verify, revoke and audit identities and credentials for authorized devices, users and processes. Furthermore, they can manage and protect physical and remote access to assets. They can also protect network integrity through network segregation and network segmentation as well as proof identities. These are bound to credentials and asserted in interactions. Lastly, organizations can authenticate users, devices, and other assets (e.g., single-factor, multi-factor).
Data Security:
This constituent requires protection of both data-at-rest and data-in-transit along with formal management of assets throughout removal, transfers, and disposition. Moreover, it implements protections against data leaks, while using integrity checking mechanisms to verify software, firmware, and information integrity.
Information Protection:
To ensure that information stays protected, RPM providers will need to conduct, maintain and test backups of information as well as destroy data according to policy. Similarly, it is pertinent to create and manage response plans (e.g. Incident Response and Business Continuity) and recovery plans (e.g. Incident Recovery and Disaster Recovery). Lastly, they need to test response and recovery plans while developing and implementing vulnerability management plans.
Maintenance:
Maintenance and repair of performed and logged organizational assets needs to be undertaken with approved and controlled tools. Furthermore, it is integral that remote maintenance of organizational assets is approved, logged, and performed in a manner that prevents unauthorized access.
Protective Technology:
Lastly, to protect RPM data audit/log records need to be determined, documented, implemented, and reviewed in accordance with policy. Moreover, besides safeguarding communication and control networks, organizations need to incorporate the principle of least functionality by configuring systems to provide only essential capabilities.
iii) Detect:
Under this framework, organizations detect anomalies and events as well as ensure continuous security monitoring.
Anomalies & Events:
A baseline of network operations and expected data flows for users and systems is established and managed. Furthermore, there needs to be an analysis of detected events to understand attack targets and methods.
Security Continuous Monitoring:
This aims to monitor network and physical environments to detect potential cybersecurity events and perform vulnerability scans. Likewise, it is essential to detect malicious code and unauthorized mobile code, while monitoring unauthorized personnel, connections, devices, and software.
iv) Respond:
This next security framework component encourages digital health solution providers to undertake response planning and improve systems. While the response plan is executed during or after an event, response improvements need to be undertaken to incorporate lessons learned as well as update response strategies.
v) Recover:
The last component of the security framework is recovery planning whereby a recovery plan is executed during or after a cybersecurity event.
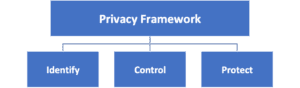
Privacy Framework:
i) Identify:
The first component of the privacy framework is identification, which is done through inventory and mapping along with risk assessment.
Inventory & Mapping:
It is important to inventory systems, products and services that process data. Furthermore, owners or operators such as service providers, partners, customers, and developers as well as their roles with respect to the systems, products, services and components (internal or external) that process data also need to be inventoried. Likewise, the data processing environment is also identified, which can include geographic location, internal, cloud and/or third parties.
Risk Assessment:
This analysis allows potential problematic data actions and associated problems to be identified. This information, coupled with likelihood and impact assessment, can be used to determine and prioritize risk mitigation. Once risks are identified, risk responses can be categorized, prioritized, and implemented.
ii) Control:
This element ensures that data is destroyed according to policy. Similarly, audit/log records are determined, documented, implemented, and reviewed in accordance with policy and incorporating the principle of data minimization.
iii) Protect:
Like the cybersecurity framework, data protection is also an integral part of the privacy framework. Both frameworks overlap on identity management, authentication, and access control, data security, maintenance and use of protective technology.
Thus, after discussing the RPM and associated security frameworks, this comprehensive framework provided by NIST, details a distributive architecture as an RPM security solution.
RPM Security Architecture
Under this solution, the following three components are defined:
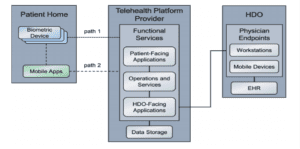
- Patient’s home
This is the environment in which the patient lives and uses RPM components that include biometric monitoring devices, devices that the patient uses to communicate with their caregivers, and devices that the patient operates for personal use.
- Telehealth platform provider
These include cloud-hosted telehealth platform providers which maintain components that include virtual or physical components with servers to manage, maintain, and receive data communications from either the patient home or the HDO.
- Health Delivery Organization (HDO)
The HDO maintains its own environment and includes workstations and clinical systems components to receive, interpret and record patient data in an electronic health record (EHR) system.
The figure below shows the high-level RPM distributed architecture.
Source: NIST Special Publication 1800-30B, Securing Telehealth Remote Patient Monitoring Ecosystem
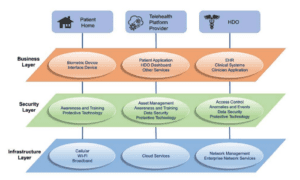
Layering the Architecture:
The above distributed architecture is then layered further across all three components. These layers comprise of:
- Business Layer: This focuses on functional capabilities that include biometric readings and patient interactions.
- Security Layer: The includes the cybersecurity and privacy security frameworks, as discussed above.
- Infrastructure Layer: This represents the network and communications environment.
The figure below a high-level view of the three layers intersecting each domain of these components.
Source: NIST Special Publication 1800-30B, Securing Telehealth Remote Patient Monitoring Ecosystem
Conclusion
COVID-19 has undoubtedly increased HDOs reliance on telehealth and RPM to reduce hospital visits and provide care at home, given its cost-effectiveness and convenience. However, with rising RPM adoption comes the added risk of exposure to security threats and vulnerabilities. Thus, it is essential to employ cybersecurity and privacy controls to ensure RPM resilience. As we discussed, since all participants (patients, telehealth providers and HDOs) engaged in RPM solutions use, manage, and maintain their separate technology components, they must all be responsible for safeguarding against threats and risks within their own domain.
Furthermore, the above security framework discussed controls that need to be implemented by HDOs and their digital health partners. Telehealth platform providers need to ensure that RPM components are isolated within the patient’s home as well as end-to-end data security is provided between the patient and HDO. Moreover, technology solutions alone cannot comprehensively tackle all the associated RPM security risks. To assure confidentiality, integrity and availability of an RPM solution, it is important to implement a holistic risk mitigation strategy that simultaneously involves people, processes and technology.
As leading RPM solutions providers, our partner company LocateMotion (SenSights.ai) ensures that their products meet all the necessary security standards to provide smart digital health solutions to patients, caregivers, and healthcare providers.
Who are We?
A niche IT solutions and professional services provider, Markitech, developer of LocateMotion (SenSights.ai), is a digital transformation company based in the US and Canada, with software engineers and data scientists primarily focused on developing artificial intelligence (AI) applications for the healthcare and telecommunications industries.
We provide services such as custom application development and prototypes, innovative end-to-end solutions leveraging AI/5G/Cloud/IoT, creative UI/UX designs, iOS/Android mobile, web and wearable app development and staff augmentation tools and training programs. Markitech has completed several game changing solutions including SenSights.ai, vEYEtals, YourDoctors.Online, Signia, and many more.
Book a free consultation today to see how can help digitally transform your business at https://markitech.ca/our-services/
Follow us on LinkedIn at @Markitech for more updates.
Contributor: Mariam Javed