Table of Contents
ToggleIncludes expert opinion from WIRED Blog, written by ANDY GREENBERG AND KIM ZETTER.
I often tell the story of how Dick Cheney’s (Ex-VP of United States) heart pacemaker which was connected to the hospital, was potentially at a risk of being hacked by terrorists. On the bright side, I also tell the story of how Tesla remotely rebooted their car’s software, thus raising the car height and hence successfully avoiding recalls worth billions.
These certainly are extreme examples of IoT security concerns and benefits. During our Yourdoctors.online legal search with top lawyers in Canada and US, we were told that patient records (because it is personal information) are even more sought after as compared to credit card information. Although that has seemingly nothing to do with IoT, it has brought to light the fact that as the world becomes more connected, we are becoming more vulnerable. Today, cheap, radio-connected computers have invaded our world. We are already surrounded by sensors all around us, constantly monitoring and recording our personal information. These sensors will soon be embedded in everything from our houses to our toys, phones and cars to even our bodies. And this year has made it clearer than ever before that the Internet of Things introduces all the vulnerabilities of the digital world into our real world.
In recent news, security researchers poked holes in everything from Wi-Fi-enabled Barbie dolls to two-ton Jeep Cherokees. I remember the recent days soon after the sad demise of Blackberry when Google introduced its new platform Android . Many security concerns were raised at that time as well. I agree with the entrepreneur Chris Rouland that, similar to Android, for now these anticipated vulnerabilities have yet to manifest themselves in real-IoT world. But the fact that Rouland, (who once ran the controversial government hacking contractor firm Endgame), has bet his next company, an Internet-of-Things-focused security startup called Bastille, on the risks of hackable digital objects, should be enough to cause serious concern about the potential security issues surrounding IoT.
Here are a few of the hacks that made 2015 the year of insecure internet things:
Jeep Cherokee, Tesla and other AUTOMOBILES can get hacked
I found this recent story on WIRED really interesting. Security researchers Charlie Miller were able to alter the automobile industry’s notion of “vehicle safety” in 2015 when they demonstrated for WIRED that they could remotely hack a 2014 Jeep Cherokee to disable its transmission and brakes. Their work led Fiat Chrysler to issue an unprecedented recall for 1.4 million vehicles, mailing out USB drives with a patch for the vulnerable infotainment systems and blocking the attack on the Sprint network that connected its cars and trucks.
That Jeep attack turned out to be only the first in a series of car hacks that rattled the auto industry through the summer. At the DefCon hacker conference in August, Marc Rogers, principal security researcher 
One can take control of MEDICAL DEVICES remotely
Remember the example of Dick Cheney’s pacemaker being shut remotely as it was connected to the hospital. Hacking cars are no longer the only way to cause fatalities in the Internet of Things realm . Critical medical equipment and devices also have software and architecture vulnerabilities that would let malicious actors hijack and control them, with potentially deadly consequences. Keeping the above mentioned security risks in view, Dick Cheney’s cardiologist, fearing that an attacker could deliver a fatal shock to the then vice president through his 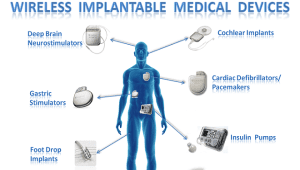
The Federal Drug Administration, which oversees the safety approval process of medical equipment, has taken note of the problems found in all of these devices and others and is beginning to take steps to remedy them. The federal agency began working this year with a California doctor to find a way to fix security problems found in insulin pumps specifically. But the remedies they devise for these pumps could serve as a model for securing other medical devices as well.
Unfortunately, many of the problems with medical devices can’t be fixed with a simple software patch—instead, they require the systems to be re-designed. All of this takes time, however, which means it could be years before hospitals and patients see more secure devices.
How about taking control of sniper GUNS remotely?
Not even guns have been spared from the risks of hacking. Married hacker couple Runa Sandvik and Michael Auger in July showed WIRED that they could take control of a Wi-Fi-enabled TrackingPoint sniper rifle. Sandvik and Auger exploited the rifle’s insecure Wi-Fi to change variables in the gun’s self-aiming scope system, allowing them to disable the rifle, make it miss its target, or even make it hit a target of their choosing instead of the intended one. “There’s a message here for TrackingPoint and other companies,” Sandvik told WIRED at the time. “When you put technology on items that haven’t had it before, you run into security challenges you haven’t thought about before.” That rule certainly applies to any consumer-focused company thinking of connecting their product to the Internet of Things. But for those whose product can kill—whether a gun, a medical implant, or a car—let’s hope the lesson is taken more seriously in 2016.
In conclusion, having developed IoT products for more than 5 years and now leading a team which focuses on designing, developing and commercialization of IoT and Enterprise Apps, I firmly believe that security should be a huge concern for almost all verticals who plan to take advantage of the interesting and exploding world of IoT, Big Data and Cloud. You can reach me at nauman.jaffar@markitech.ca; for further details on how we can help you explore this exciting new digital world or click here for a 30 minute free consultation with our C-Level experts.
[cta]
Do you have a passion for IoT?
Want to learn more about the possibilities of IoT in the future and for your business?
Join on IoT peer group.
[su_button url=”http://www.techconnex.ca/event-2100498?CalendarViewType=1&SelectedDate=1/18/2016&utm_source=MarkiTech+Team&utm_campaign=4d63797686-January_Newsletter12_23_2015&utm_medium=email&utm_term=0_b604d9a514-4d63797686-” background=”#ef6d2d” size=”15″ rel=”lightbox”]Register Now[/su_button]


